ISO 27001 is part of a set of standards developed to handle information security: the ISO/IEC 27000 series. Its full name is “ISO/IEC 27001 – Information security, cybersecurity and privacy protection — Information security management systems — Requirements.”
ISO 27001 is a widely used standard for Information Security Management Systems referred to as an ISMS.
How does ISO 27001 work?
The focus of ISO 27001 is to protect the confidentiality, integrity, and availability of the information in a company. This is done by finding out what potential incidents could happen to the information (i.e., risk assessment), and then defining what needs to be done to prevent such incidents from happening (i.e., risk mitigation or risk treatment).
Therefore, the main philosophy of ISO 27001 is based on a process for managing risks: Find out where the risks are, and then systematically treat them, through the implementation of security controls (or safeguards).
ISO 27001 requires a company to list all controls that are to be implemented in a document called the Statement of Applicability.
What are the ISO 27001 controls?
The ISO 27001 controls (also known as safeguards) are the practices to be implemented to reduce risks to acceptable levels. Controls can be technological, organizational, physical, and human-related.
How many controls are there in ISO 27001?
The 2022 revision of ISO 27001 Annex A lists 93 controls organized into four sections numbered A.5 through A.8, as explained below.
Two parts of the standard
The standard is separated into two parts. The first (main) part consists of 11 clauses (0 to 10). The second part, called Annex A, provides the guidelines for 93 control objectives and controls.
Clauses 0 to 3 of the main part of the standard (Introduction, Scope, Normative references, Terms and definitions) serve as an introduction to the ISO 27001 standard. Clauses 4 to 10, which provide the ISO 27001 requirements, are mandatory if the company wants to be compliant with the standard, and are examined in more detail later in this article.
Annex A of the standard supports the clauses and their requirements with a list of controls that are not mandatory, but that are selected as part of the risk management process.
How do you implement ISO 27001 controls?
- Organizational controls (Annex A section A.5) are implemented by defining the rules to be followed, as well as expected behavior from users, equipment, software, and systems. E.g., Access Control Policy, BYOD Policy, etc.
- People controls (Annex A section A.6) are implemented by providing knowledge, education, skills, or experience to persons to enable them to perform their activities in a secure way. E.g., ISO 27001 awareness training, ISO 27001 internal auditor training, etc.
- Physical controls (Annex A section A.7) are primarily implemented by using equipment or devices that have a physical interaction with people and objects. E.g., CCTV cameras, alarm systems, locks, etc.
- Technological controls (Annex A section A.8) are primarily implemented in information systems, using software, hardware, and firmware components added to the system. E.g., backup, antivirus software, etc.
Two parts of the standard
The standard is separated into two parts. The first (main) part consists of 11 clauses (0 to 10). The second part, called Annex A, provides the guidelines for 93 control objectives and controls.
Clauses 0 to 3 of the main part of the standard (Introduction, Scope, Normative references, Terms and definitions) serve as an introduction to the ISO 27001 standard. Clauses 4 to 10, which provide the ISO 27001 requirements, are mandatory if the company wants to be compliant with the standard, and are examined in more detail later in this article.
Annex A of the standard supports the clauses and their requirements with a list of controls that are not mandatory, but that are selected as part of the risk management process.
What are the requirements for ISO 27001?
The requirements from clauses 4 through 10 can be summarized as follows:
Clause 4 of ISO 27001 – Context of the organization – One prerequisite of implementing an Information Security Management System successfully is understanding the context of the organization. External and internal issues, as well as interested parties, need to be identified and considered. Requirements may include regulatory issues, but they may also go far beyond.
With this in mind, the organization needs to define the ISMS scope.
Clause 5 of ISO 27001 – Leadership – The requirements of ISO 27001 for adequate leadership are manifold. The commitment of the top management is mandatory for a management system. Objectives need to be established according to the strategic direction and objectives of the organization. Providing resources needed for the ISMS, as well as supporting persons in their contribution to the ISMS, are other examples of the obligations to meet.
Furthermore, the top management needs to establish a top-level policy for information security. The company’s ISO 27001 Information Security Policy should be documented, as well as communicated within the organization and to interested parties.
Roles and responsibilities need to be assigned, too, in order to meet the requirements of the ISO 27001 standard and to report on the performance of the ISMS.
Clause 6 of ISO 27001 – Planning – Planning in an ISMS environment should always take into account risks and opportunities. An information security risk assessment provides a key foundation to rely on. Accordingly, information security objectives should be based on the risk assessment. These objectives need to be aligned with the company`s overall objectives, and they need to be promoted within the company because they provide the security goals to work toward for everyone within and aligned with the company. From the risk assessment and the security objectives, a risk treatment plan is derived, based on controls as listed in Annex A.
Clause 7 of ISO 27001 – Support – Resources, competence of employees, awareness, and communication are key for supporting the ISMS. Another requirement is documenting information according to ISO 27001. Information needs to be documented, created, and updated, as well as being controlled. A suitable set of documentation, including a communications plan, needs to be maintained in order to support the success of the ISMS.
Clause 8 of ISO 27001 – Operation – Processes are mandatory to implement information security. These processes need to be planned, implemented, and controlled. Risk assessment and treatment – which need to be on top management`s minds, as we learned earlier – have to be put into action.
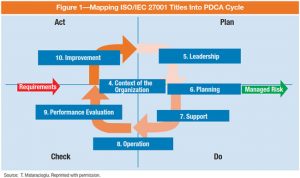
Figure 1 below provides a view of the clauses described above with the Plan, Do , Check, Act philosophy behind an ISMS.
Please create a support ticket for more information about ISO 270001. We are able to assist with a practical assessment and implementation services with you.
Source: advisera.com
